Configuring Domain Controllers to use fixed RPC ports behind firewalls
July 26, 2011 4 Comments
Well here goes…my first post.
A while ago we had some issues getting our domain controllers to replicate properly behind our edge firewalls (we have lots of remote dc’s for our remote sites). I had read through all the Microsoft technotes on how to configure dc’s for this but it all seemed rather vague and lacked real clarity.
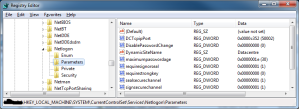
I configured them using a group policy that defined the settings mentioned in this kb article: http://support.microsoft.com/kb/224196 and thought that everything was ok…until we started having replication issues and clients unable to authenticate to remote dc’s.
After more digging I found another article mentioning client RPC dynamic port allocation: http://support.microsoft.com/kb/154596 but this didn’t specifically talk about AD replication and authentication.
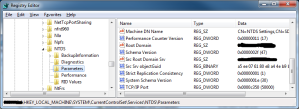
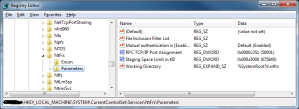
I ended up engaging Microsofts Premier Support and a case was raised. I had a few discussions via email and phone with one of their techs who suggested that I also add this registry setting in addition to the two mentioned in kb224196 (ntds and netlogon services) which is covered in this article http://support.microsoft.com/kb/319553
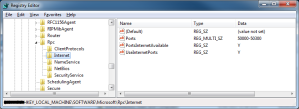
He then also recommended fixing a range of ports for dynamic RPC as mentioned in the article I had previously read: http://support.microsoft.com/kb/154596
This lead me to have the following settings applied to my dc’s:
Note that the dynamic port assignment had to be done as a manual reg file as you can’t create an ADM template that uses the data type of REG_MULTI_SZ, hence it can’t be done via group policy (without using a logon script, etc).
This seemed to work at first until I discovered that we still had issues with our 2008 R2 dc’s. The MS tech was at a loss as to why these settings had not worked for all of our dc’s. I stumbled across this technet post: http://social.technet.microsoft.com/Forums/en-ZA/winserverNIS/thread/91b6f99d-53d5-4d1c-b07f-d3651e302fa4.
I suggested to the tech that maybe the 2008 R2 dc’s needed their dynamic RPC ports set using the netsh command. He could not find anything in his internal knowledge base and went on to say that his test environment was 2003 only, at which point he recommended I apply the dynamic RPC port settings using this method.
So, in the end we had three reg fixes for ALL dc’s, 2003 and 2008, that statically assign a port for NTDS, NTFRS and Netlogon services (each must be a different port in the dynamic range). Then for all 2003 dc’s we applied the dynamic RPC port assignment as per article KB154596 and for all 2008/R2 dc’s we applied the netsh command to set these RPC ports (as per this article: http://support.microsoft.com/kb/929851).
Eventually we had all of our dc’s replicating properly and clients were able to authenticate through the firewalls with no issues. Just remember to give yourself at least a few hundred ports for the dynamic range (the ntfrs, ntds and netlogon can only have a single port assigned to them).
The MS tech was quite pleased to add this information to his knowledge base for his own reference 🙂 Would have been far easier if MS had pulled all of these articles together to give one easy to follow document for allowing AD to work through firewalls…
Anyway, I hope this helps others out there!



I’m in our pain box now….. I walked into the party though lol. I suppose we don’t need to hack the registry for RPC’s if we can get network security to allow the full dymanic range. I’m sorry I haven’t read through all of your articles but I’m sure I’ve been there before. It sounds like the method you used was pinning down anything in AD DS that could use RPC to the single port and left the few hundred open as the “dynamic range” but just a smaller group/hole of ports.
Did you run the commands remotely across servers via powershell or did you run it by hand? Currently have 26 DC’s and growing split between 5 child domains and a parent.
Hi James,
I feel for you mate, having firewalls between DCs can be a real pain!
We have over 50 and a lot were still at 2k3 level so the changes were done with a combination of scripts and reg files, mostly applied manually though.
The newer 2k8 ones were better as we could apply the settings using Group Policy Preferences. It would be far easier if the firewalls were able to track the RPC session id end to end so you didn’t have to create a nice big hole in them.
Good luck with your changes! Remember to keep an eye on replication!
Cheers,
Ben
Hi,
It was very useful, as review the your dynamic port define 50000-50300, it require open 50000-50300 in firewall equipment?
Best regards,
Chung
Hi Chung,
Apologies for the late reply. Yes, we had to allow these port ranges in our firewalls. Not ideal but were not prepared to go down the IPSec path.
Good luck!
Cheers,
Ben